Worms – Types and Habitats
|
Penetration of a remote system can be accomplished in any of three ways… In each case the worm arranges to get a remote command interpreter which it can use to copy over, compile and execute the 99-line bootstrap. The bootstrap sets up its own network connection with the local worm and copies over the other files it needs, and using these pieces a remote worm is built and the infection procedure starts over again. – Donn Seeley; A Tour of the Worm; University of Utah. |
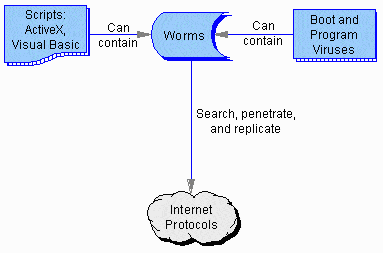
Internet worms are truly autonomous virtual viruses, spreading across the net, breaking into computers, and replicating without human assistance and usually without human knowledge.
Worms are particularly interesting technological constructs, with an intriguing mathematical structure and complexity. They fascinate because they take the digital imitation of life to another step — they autonomously search for computers, penetrate them, and replicate their intelligence to continue the process.
An Internet worm can be contained in any kind of virus, program or script. Sometimes their inventor will release them into the wild in a single copy, leaving them to replicate by themselves through a variety of stratagems and protocols.
History. Worms use a variety of methods to propagate across the Internet. Early worms simply scanned the local network drives and folders and inserted themselves into programs wherever they could, trusting human beings to move disks and directories around in the normal course of things so they could continue to spread.
Since the late 1990’s, many Internet worms have been Visual Basic script viruses which replicate on Windows computers by interacting with the user’s email program to send themselves to many (often all) of the addresses in the address book. Once on a new machine, they repeat the process with the new user’s address book, quickly expanding the number of people reached. Some of the worst outbreaks of email worms have spread around the world within just a few hours, and email remains the Internet worm’s fastest known transmission method.
Beginning in 2001, the most dangerous worms started to employ weaknesses in the Windows operating system to attack machines directly across the Internet. When a significant Windows weakness was found, Microsoft would patch it, hackers would release worms to attack it a few weeks later, and any unpatched machine connected to the Internet would soon be compromised. With several hundred million machines running Windows, statistically speaking a lot don’t get patched immediately, so there are always thousands of vulnerable systems. Even computers inside a firewall protected intranet are at risk as long as there is one weak link somewhere — an unprotected machine on the Internet able to reach the rest of the intranet. Microsoft introduced automatic operating system updates to help solve this problem.
The most successful Internet worm of all time, in terms of sheer saturation, was the code red worm, which scanned the Internet for vulnerable Windows computers running the IIS web server to install itself and continue the infection. For example, a list of the code red infected computers trying to break into the LivingInternet site on August 7, 2001, can be found here. (Fortunately, the site was running on the Apache web server.)
A wide range of other inventive strains of Internet worms have employed security weaknesses in IRC, MAPI, sendmail, finger, and other programs and protocols. A few worms began to be discovered for Linux in the late 1990’s as it became more popular across the Internet and some vulnerabilities were found, but the strong security architecture of Linux has kept the number of problems relatively low.
The first worm. The first worm disabled most of the Internet then existing. Robert Morris, a Computer Science graduate student at Cornell University and (embarrassingly) son of the Chief Scientist at the National Computer Security Center, wrote a 99 line program in the C language designed to self-replicate and propagate itself from machine to machine across the Internet. The worm performed the trick by combining a bug in the debugging mode of the sendmail program used to control email on almost all Internet computers, a bug in the finger program, and the Unix rexec and rsh commands.
On November 2, 1988, Morris released his worm, but did so from an MIT computer to disguise his origin. In his view, only one thing went wrong — the worm started replicating at a much faster rate than he had predicted, and began crashing and disabling computers across the Internet.
Morris sent out an anonymous message telling people how to disable the worm, but because it had brought down the Internet, the message about how to disable it couldn’t get through. The worm eventually infected more than 6,000 computers across the Internet. Within a day teams of programmers at the University of California at Berkeley and Purdue University reverse engineered the worm and developed methods of stopping it. The Internet then came back to normal in a couple of days.
Morris claimed that he had intended his worm as an innocent experiment and hadn’t planned it to have any negative effects. Nonetheless, he was eventually convicted of violating the computer Fraud and Abuse Act (Title 18), and sentenced to three years of probation, 400 hours of community service, and a $10,050 fine. His appeal was rejected in March, 1991.
At least one good thing resulted from this incident — the Computer Emergency Response Team, or CERT, was formed by ARPAin response to the Morris worm incident to track and provide information on Internet security threats.