Boot & Program Viruses – Types and Habitats
Boot and program viruses were the first viruses. They are generally made of executable code that hides inside device boot programs and application programs, and are usually targeted for a specific computer operating system. These were the earliest types of computer viruses, and remained relatively common in the wild until overtaken in 1998 by script and macro viruses.
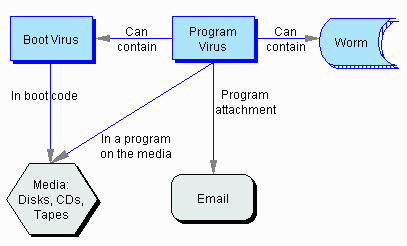
Boot viruses. Boot viruses hide in the boot code for a media device, such as a disk or CD, and run automatically when the media is loaded since boot programs are always the first code loaded from any device. Boot viruses proliferated on floppy disks and even CD’s into the late 1990’s, but aren’t seen as often these days with the decline in importance of transferable, bootable media.
The first computer boot virus was built by a 15 year old kid named Rich Skrenta in 1982 for Apple II computers. Called “Elk Cloner”, it would activate whenever a floppy disk was booted on a computer, install itself on the computer, and then infect other disks used later. Once every 50 times an infected floppy was inserted in a computer it would display the following message.
Elk Cloner: The program with a personality
It will get on all your disks
It will infiltrate your chips
Yes it’s Cloner!
It will stick to you like glue
It will modify ram too
Send in the Cloner!
Skrenta launched the virus into the wild in early 1982 by infecting his school’s computer and giving out disks at a computer club. Since viruses were not yet known and there were no safegaurds, it spread around the country and continued to pop up on Apple II computers for years afterwards.
The first boot virus to infect Microsoft computers was called Brain, created in 1986 by two Pakistani brothers, and displayed the phone number of their computer repair business.
Program viruses. Program viruses can travel on media like a CD or across the Internet by email attachment. They hide in an apparently useful program and then run when the program is opened. They are often called trojan horse viruses, after the hollow wooden horse containing soldiers that Ulysses and the Greeks gave to Minerva during the Trojan war, and from which the soldiers emerged that night to open the gates of the city of Troy to the Greek armies, thereby causing the city’s downfall.
Program viruses may be deliberately hidden in a program by the developer, or surreptitiously attached after the fact at some point along its travels from computer to computer. Program viruses are also sometimes the vector of infection for boot viruses and worms.
Virus infection. A greeting card program emailed to you from a friend might display a holiday animation and song, while at the same time installing a remote access virus program that gives a distant hacker control over your computer whenever you’re connected to the Internet. Similarly, a shareware program downloaded and emailed to you by another friend might have been infected with a virus on his computer or the server where it was stored.
The first thing a boot or program virus often does is insert commands and settings in the operating system so that they can operate freely, undetected, and unaudited, without warning messages or access log records. Some of them even change the Basic Input Output System (BIOS) that interfaces between the computer’s hardware and software to help mask their activities.
The most sophisticated program viruses include “stealth viruses”, which encrypt their contents to try and avoid detection by virus protection software, and “polymorphic viruses”, which alter their content every time they replicate to try and avoid detection, which exhibits behavior just like real viruses. Most anti-virus programs can still catch most of these types of viruses.