Script Viruses – Types and Habitats
Script viruses (sometimes called macro viruses) generally travel embedded in email and office automation documents, although they can be found in web pages as well.
Old fashioned program viruses are usually implemented in executable system code, whereas script viruses are usually written in a powerful high-level language that is compiled and run on the fly. They often have sophisticated functionality and direct interfaces to high level applications such as word processing, spreadsheet, email, and web programs, and can wreak considerable havoc. Since they first surfaced in office automation programs, they are sometimes also called “macro” viruses. Script viruses can also propagate through IRC protocols.
On Microsoft computers, turning on your script checking virus protection is essential. However, keep in mind that there may be an associated performance hit for some applications. Many applications on Windows are written in Visual Basic, and real-time script virus checking can double the time it takes for their usual functions to run. If you find that ordinary functions take an inordinate length of time to complete, you can try temporarily turning this feature off in your anti-virus checker — but don’t forget to turn it back on afterwards!
Active threats. The following types of script viruses are currently the most active and dangerous, on the Windows platform:
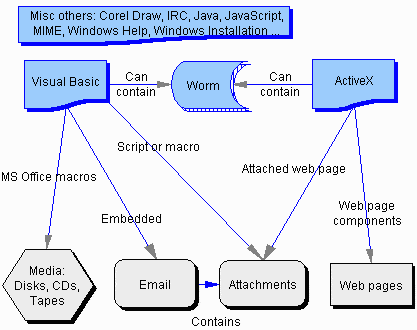
- Visual Basic is a flexible and powerful programming environment for Microsoft Windows, Office, and Internet applications. Script viruses written in Visual Basic can run throughout the Microsoft architecture, giving them considerable reach and power, and making them the primary virus threat today.
The first widespread Visual Basic script virus was Melissa, which brought down several of the large international corporations for several days in March 1999. Melissa traveled in a Microsoft Word document and ran when the document was opened, then opened the associated Microsoft Outlook email program, read the user’s email address book, and then sent email copies of itself to the first fifty names it found. It spread very quickly.
The Melissa virus architecture was quickly followed by many similar variants programmed by hackers around the world, including the ground breaking KAK, the first Visual Basic script virus that triggered as soon as an email was opened. KAK was then followed by BubbleBoy, which triggered if an email was even viewed in the preview pane. A steady stream of Visual Basic script viruses continue to circulate to this day. There are even automated, point and click programs like VBS Love Generator to help hackers produce additional variants. Script viruses which use email to send themselves to others are also a form of worm.
The term “macro virus” is used less often, and generally refers to a virus in an office automation application macro, most commonly a Visual Basic macro in a Microsoft Word or Excel document. Macro viruses can cross system boundaries from Windows to Macintosh computers with MS Office documents. Current versions of Microsoft Office contain strong anti-macro protections to guard against known attacks.
- ActiveX is one of Microsoft’s distributed application technologies that enable web pages to download programs on the fly with the full power of any executable running on your machine. This makes ActiveX modules especially efficient and powerful, but also a security risk since they can create, change, and delete files, add system programming code, or take any other action your user account is allowed on your computer.
To help mitigate the risk, Microsoft provides a network architecture of encrypted security certificates for ActiveX modules. This network gives you the option of refusing the download of unsigned ActiveX modules from unknown authors, and at least disclosing the signed identity of those modules that you do accept in case they later cause problems. However, this approach is not universally accepted by the general user and professional security communities, and is sometimes called “trust me now, try to catch me later”. Users running Internet Explorer on Windows machines should make sure that their browser security settings are set to “disable” for unsigned ActiveX applets, and to “prompt” for signed applets.
Hypothetical threats. The following script viruses are largely theoretical, but illustrate that they can turn up wherever there is scripting code:
- Java is a standard cross platform development environment, and is often used to download scripts to add functionality like a clock or chat room interface to a web page. Java was written with a strong security model which protects your computer’s data and resources, and it has so far proved remarkably resistant to script virus infection. You can turn Java off in your browser if you want to be extra careful, but it will disable some useful functionality on some web pages.
- JavaScript is the standard web programming language. JavaScript also has a well-defined security model that protects data and resources, and the few JavaScript viruses that have been discovered have been mainly theoretical in nature. You can turn JavaScript off in your browser settings if you want to be extra careful, but it will disable functionality on many web pages.
- MIME. The first script virus that triggered as soon as an email was opened was a MIME virus that applied to older versions of Netscape Mail, Microsoft Outlook, and Eudora Mail. In a variation on an old hacker technique, the attached MIME file was given a very long name that triggered a bug which allowed the end of the name to be run as a series of instructions, which could then be written to run the virus. However, a fix for the bug was quickly developed for each vulnerable email program, and MIME viruses have so far remained hypothetical.
- Others. Several other scripting environments have also had viruses, including Corel Draw, Hypertext Preprocessor, Windows Help, Windows installation files, and Windows registry files. Anywhere there is a script interpreter there is an opportunity for a script virus to run.